Thank you! Your submission has been received
The landscape of financial fraud is characterized by rapid evolution, with malicious actors continuously developing new tactics. Consequently, traditional, single-faceted defense mechanisms are increasingly proving inadequate. This document outlines the rationale and architecture for a robust, multi-layered fraud detection strategy, designed to offer resilience, adaptability, and the necessary transparency for regulatory scrutiny and operational excellence.
1. The Inadequacies of Single-Layer Fraud Defenses
Relying on a solitary defense technique exposes organizations to significant risks. The core deficiencies of such an approach include:
Rapid Obsolescence: Fraud methodologies adapt with remarkable speed, often on a weekly basis. Static rules and detection models quickly lose their effectiveness as new attack vectors emerge.
Model Degradation: Pure machine-learning models, while powerful, can experience "drift." Without a constant influx of fresh, accurately labelled data, their predictive accuracy diminishes over time, leading to a reduced ability to identify fraudulent activities.
Limited Visibility: Point solutions, such as those focused solely on device identification, user identity, or behavioral patterns, only illuminate a specific segment of the potential attack surface. This narrow focus can leave significant vulnerabilities unaddressed.
Regulatory and Audit Concerns: Regulatory bodies increasingly demand clear explanations for fraud detection and prevention decisions. "Black-box" systems, which provide scores without transparent reasoning, can create friction during audits and complicate compliance efforts.
The ultimate consequence of employing a single-threaded defense is an undesirable trade-off: organizations either implement overly aggressive measures that block legitimate customers (resulting in high false positives and poor customer experience) or they fail to detect novel and sophisticated fraud schemes, leading to financial losses and reputational damage.
2. Foundational Design Principles for a Multi-Layered Fraud Defense Stack
To construct an effective and modern anti-fraud infrastructure, several key design principles must be embraced:
Defense in Depth: This core tenet involves the strategic combination of diverse, orthogonal signals. The objective is to create a series of barriers, each employing different detection methods, compelling fraudsters to overcome multiple, distinct challenges to succeed.
Hybrid Processing (Real-Time and Batch): The system must be capable of making instantaneous decisions at the point of interaction (the "edge") to prevent immediate threats. Concurrently, it should support ongoing, background processes for model retraining, rule optimization, and deeper analytical reviews.
Prioritizing Explainability: Every layer within the defense stack should be designed to offer clear, replayable logic or facilitate post-hoc interpretation of its decisions. This is paramount for regulatory reporting, internal audits, and enabling analysts to understand and trust the system's outputs.
Integrated Feedback Loops: A crucial element for sustained effectiveness is the implementation of closed-loop feedback mechanisms. This involves systematically labeling outcomes (fraudulent vs. legitimate), feeding this data back into the system, and automating the promotion of more effective detection strategies and models.
Composable and Modular Architecture: The system should be built using a plug-and-play approach, allowing for the integration of various vendor solutions and technologies. This avoids monolithic system lock-in, promotes flexibility, and enables the organization to adapt by incorporating best-of-breed tools for specific functions.
3. The Nine Critical Layers of a Comprehensive Fraud Defense System
A state-of-the-art fraud prevention framework typically incorporates the following nine interconnected layers:
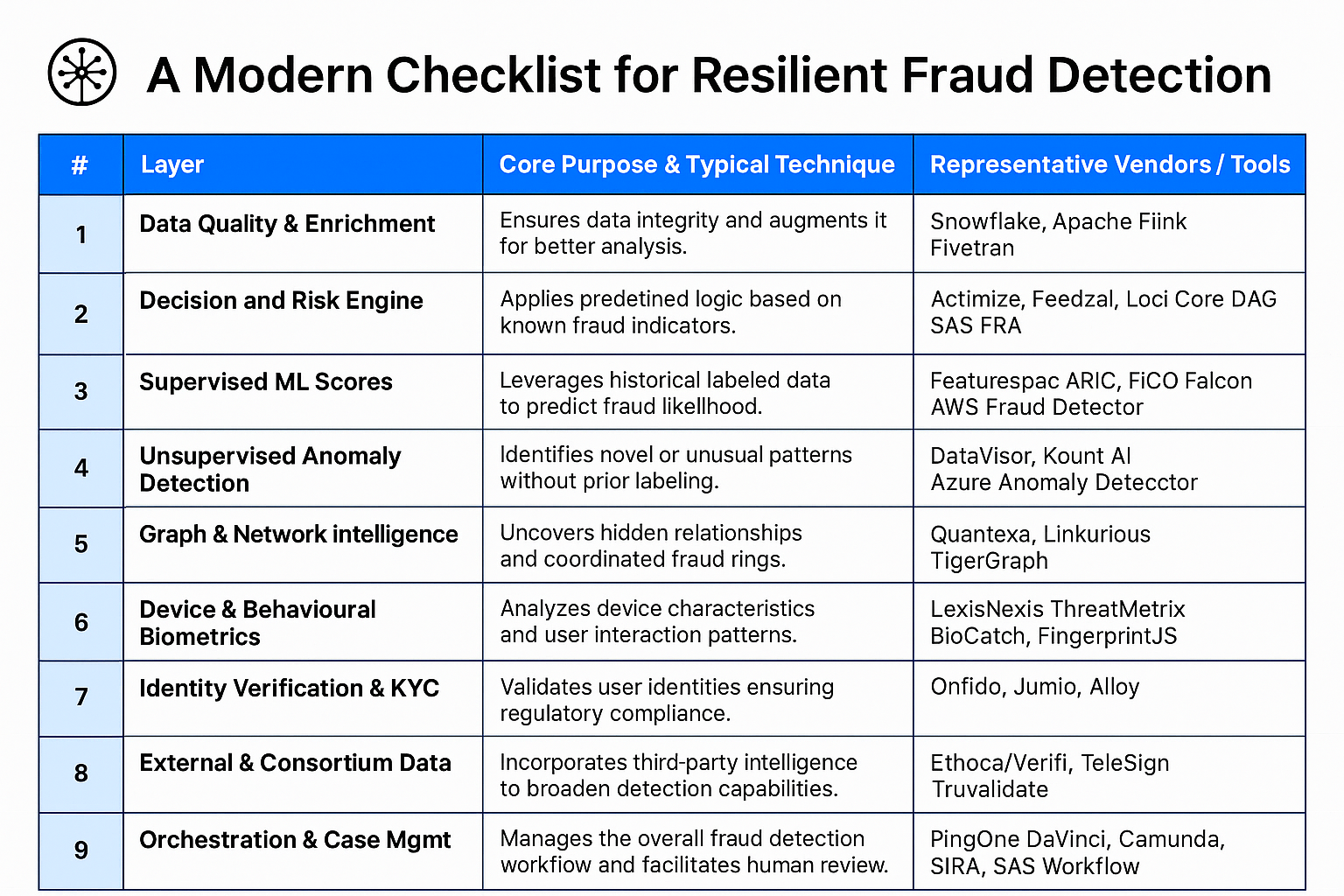
4. The Interlocking Nature of the Defensive Layers
It is critical to understand that these nine layers do not operate in isolation. Instead, they form an integrated system where each layer informs and strengthens the others. For instance, enriched data (Layer 1) improves the accuracy of both rules (Layer 2) and machine learning models (Layers 3 & 4). Insights from graph intelligence (Layer 5) can refine behavioral biometric profiles (Layer 6) or trigger enhanced identity verification (Layer 7). External data (Layer 8) can provide crucial context for alerts generated by any layer, all managed and prioritized through an orchestration engine (Layer 9) for efficient review and action. This synergy creates a defense that is significantly more robust and adaptable than the sum of its individual parts.
Conclusion: Embracing a Dynamic and Transparent Approach to Fraud Mitigation
In the face of increasingly sophisticated fraud tactics, a multi-layered defense strategy is no longer a luxury but a necessity. By adhering to principles of defense in depth, prioritizing explainability, fostering continuous improvement through feedback loops, and building a flexible, composable architecture, organizations can significantly enhance their fraud detection capabilities. This approach not only provides stronger protection against financial crime but also aligns with the increasing demands of regulators for transparency, accountability, and effectiveness in fraud management systems. For fraud analysts, this framework offers a comprehensive toolkit to dissect complex fraud patterns and contribute to a resilient and adaptive defense posture.
